Category: Computer
-

Robots and Chatbots
Before ChatGPT, human looking robotics defined AI in the public imagination. That might be true again in the near future. With AI models online, it’s awesome to have AI automate our writing and art, but we still have to wash the dishes and chop the firewood. That may change soon. AI is finding bodies fast…
-
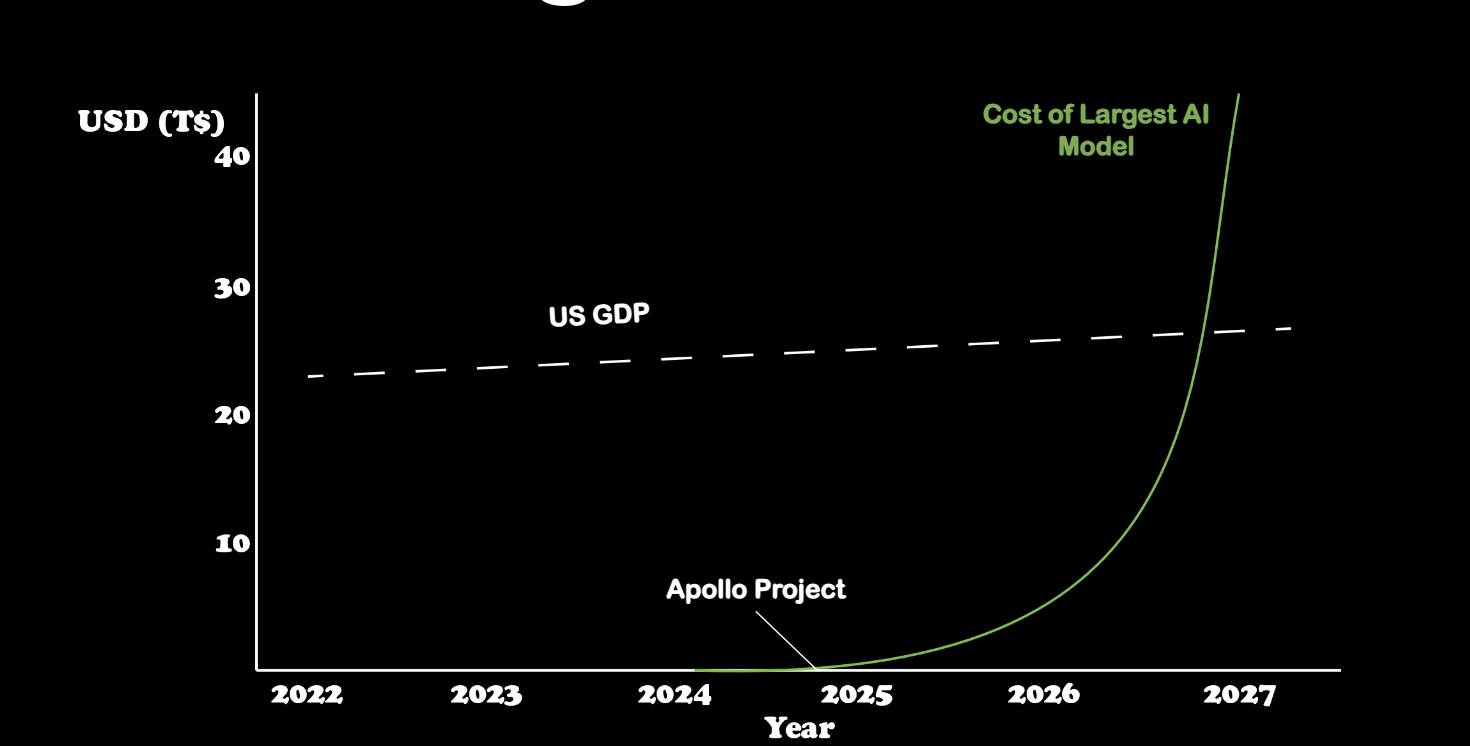
Power and AI
The Growing Power Needs for Large Language Models In 2024, AI is awesome, empowering and available to everyone. Unfortunately, while AI is free to consumers, these models are expensive to train and operate at scale. Training them is expected to be the most expensive thing ever. Yes, more than the Manhattan project, pyramids and the…
-

All those wireless Mice! (from Taiwan)
If you are like us, you get too many mice and keyboards lying around. With 5 or six devices, and an equal number of receivers you can just plug stuff in to find what matches. That assumes the peripherals are working and haven’t been lost. Can we interrogate the usb receivers and discover their associated…
-
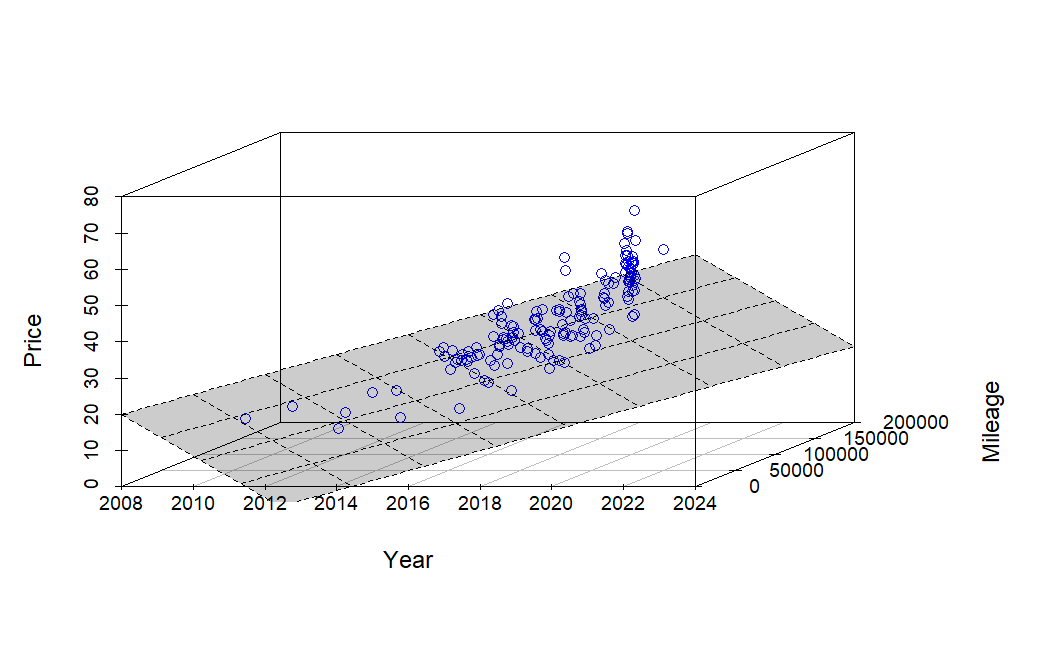
Quick(ish) Price Check on a Car
So, is it a good price? With my oldest daughter heading off to college soon, we’ve realized that our family car doesn’t need to be as large as it used to be. We’ve had a great relationship with our local CarMax over the years, and we appreciate their no-haggle pricing model. My wife had her…
-
Autoscoring with Matlab
While I qualified a long time ago on the M9, I never really learned to be a good shot. Now, I’m trying to learn to shoot well and wanted to automatically score my targets, keep the data, and get better. There are apps to do this, but none of them did what I wanted. One…
-
Nginx With Https for Local Development
Testing HTTPs locally is always hard, but I’m against testing on production or even on a remote server. Things are also complicated by developing in linux as a subsystem on windows via WSL2. I was able to use mkcert to get ssl to work locally. While I would love to use Let’s Encrypt locally, Let’s…
-
Organize Images
I deleted and recovered a large number of photos (thanks foremost). However, a large number of images from a browser cache was messing up my photo library. Who wants to keep 10,000 of these images stored on my harddrive? I used the number of unique colors to filter them out via MATLAB. As expected, if…
-
DEFCON 25 Writeup
Nothing delivers the fear of missing out like DEFCON. So much to learn and so little time. Too busy hacking in the IOT village or catching up with old friends to sit in on the talks? Read below to find out what you missed in my talk writeups below. They are listed in chronological order,…
-
Common Mathmatical Libraries: Computation, History, and Trust
A common complaint among engineers is that modern computers obscure the details of the complicated math they produce. We cringe when children are exalted as “knowing computers” from a young age. Bill Gosper and Richard Greenblatt had perhaps the maximum benefit to “learn computers”. They didn’t have wolfram alpha or even spreadsheets, they had to…
-
Satisfiability modulo theories and their relevance to cyber-security
Cybersecurity and cryptoanalysis is a field filled with logic puzzles, math and numerical techniques. One of the most interesting technical areas I’ve worked goes by the name of satisfiability modulo theories (SMT) and their associated solvers. This post provides a layman’s introduction to SMT and its applications to computer science and the modern practice of learning…